Cybersecurity Certifications
Last Updated on : 2024-06-14 20:18:20download
Across the globe, a myriad of cybersecurity regulations are being introduced in various countries and regions. In the IoT industry, cybersecurity certifications are gaining heightened importance for both brand owners and consumers. Contemporary cybersecurity regulations and standards, believed to have originated in Europe, are now expanding globally. This topic describes the global standards for certifying the cybersecurity of IoT products.
Overview
In a nutshell, cybersecurity can be divided into two parts: data security and communications security.
- Data security: Protect personal data and sensitive device data.
- Communications security: Assess the vulnerabilities in IoT devices that can be exploited by hackers, and consider the countermeasures and protection mechanisms.
| Countries and regions | Regulations and standards | Mandatory date | Regulated categories |
|---|---|---|---|
| European Union | Radio Equipment Directive (RED) 2022/30/EU 3(3)(d/e/f) on Cybersecurity | August 1, 2025 | The majority of IoT devices covered by RED, such as smart home devices, mobile phones, and connected wearables. Devices already covered by other specific directives are excluded, such as automobiles, medical devices, civil aviation, and electronic road-toll systems. |
| European Union | ETSI EN 303 645 Cybersecurity for Consumer Internet of Things: Baseline Requirements | Voluntary (broadly recognized worldwide and either directly applied or extensively cited by most countries) | Consumer IoT devices |
| United Kingdom | Product Security and Telecommunications Infrastructure Act (PSTI) | April 29, 2024 | The majority of consumer IoT products are covered, such as mobile phones, smart home appliances, smart speakers, wearable connected fitness trackers, outdoor leisure products, and connected children’s toys and baby monitors. Certain products are excluded, such as desktop computers, laptop computers, vehicles, smart meters, smart charge points (for electric vehicles), and medical devices. |
| United Kingdom | Engineering Recommendation (EREC) G99 and G98 | April 27, 2019 | EREC G98 applies to micro-generators (up to and including 16 A per phase). EREC G99 applies to all devices not covered by EREC G98. |
| Finland | Finnish Cybersecurity Label | Voluntary | Smart connected products |
| Germany | IT Security Label | Voluntary | IoT devices |
| United States | H.R. 1668: IoT Cybersecurity Improvement Act of 2020 Public Law 116-207 |
December 4, 2020 | IoT devices (The Act focuses on IoT devices used by the federal government) |
| California, USA Oregon, USA |
A.B. 1906 and S.B. 327 House Bill 2395 |
January 1, 2020 | Connected devices for sale |
| United States | NISTIR 8259A: IoT Device Cybersecurity Capability Core Baseline | Voluntary (widely recognized in the United States) | IoT devices |
| United States | NISTIR 8425: Profile of the IoT Core Baseline for Consumer IoT Products | Voluntary (widely recognized in the United States) | Consumer IoT devices |
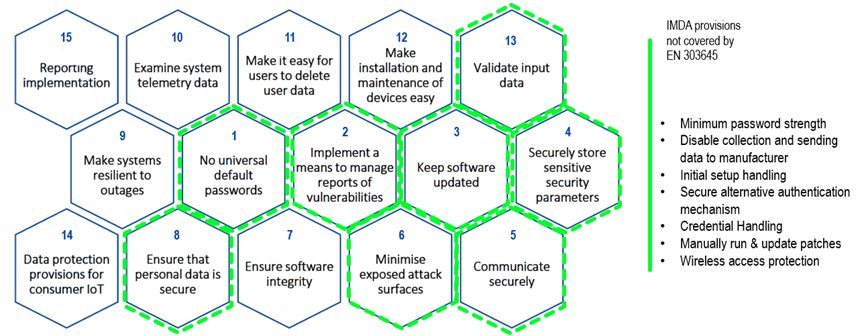
| Singapore | IMDA Security Requirements for Residential Gateways (IMDA TS RG-SEC) | April 12, 2021 | Home routers and residential gateways |
| Singapore | Security Requirements to Guard against Network Storms for Cellular Devices (IMDA TS CD-SEC) | January 2, 2023 | Cellular devices |
| Singapore | Cybersecurity Labelling Scheme (CLS) | March 2020, partly mandatory |
|
| Japan | MIC Article 34-10 Amendment | April 1, 2020 | Terminal equipment that uses Internet Protocol and configurable private lines, including routers and web cameras. |
| Vietnam | 736/QĐ-BTTTT: List of Baseline Cybersecurity Requirements for Consumer Internet of Things (CIoT) Devices | Voluntary | Consumer IoT devices |
| Brazil | Act 77/2021: Cybersecurity Requirements for Telecommunications Equipment | July 1, 2021 | All products that have the function of terminal equipment with an internet connection or telecommunications network infrastructure equipment. |
| Brazil | Act 2436/2023: Minimum Cybersecurity Requirements for Assessing the Conformity of CPE (Customer Premises Equipment) | March 10, 2024 |
|
| Australia | Code of Practice: Securing the Internet of Things for Consumers | Voluntary | Consumer IoT devices |
| Global | IEC 60335-1:2020 (Ed. 6.0) Safety of Household and Similar Electrical Appliances - Part 1: General Requirements, Annex U | To be determined. IEC standards may be referenced in regulations and standards of different countries, but the extent to which Annex U is mandatory can vary by country. | Smart home appliances |
- California Senate Bill 327 and Assembly Bill 1906 are essentially the same bill.
- U.S. Public Law 116-207 requires the National Institute of Standards and Technology (NIST) to develop and publish standards and guidelines for the development, management, configuration, and patching of IoT devices.
ETSI EN 303 645
ETSI EN 303 645, a globally applicable standard for consumer IoT, is designed to prevent large-scale attacks against IoT devices by establishing a security and privacy baseline for connected consumer products and provides a basis for future IoT certification schemes. It also supports products’ compliance with the EU GDPR. It covers the security requirements for devices, communications, and personal data protection. The standard outlines 15 cybersecurity provisions for consumer IoT.
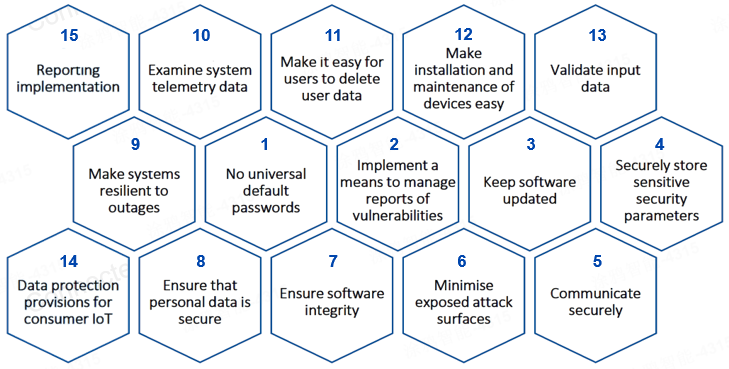
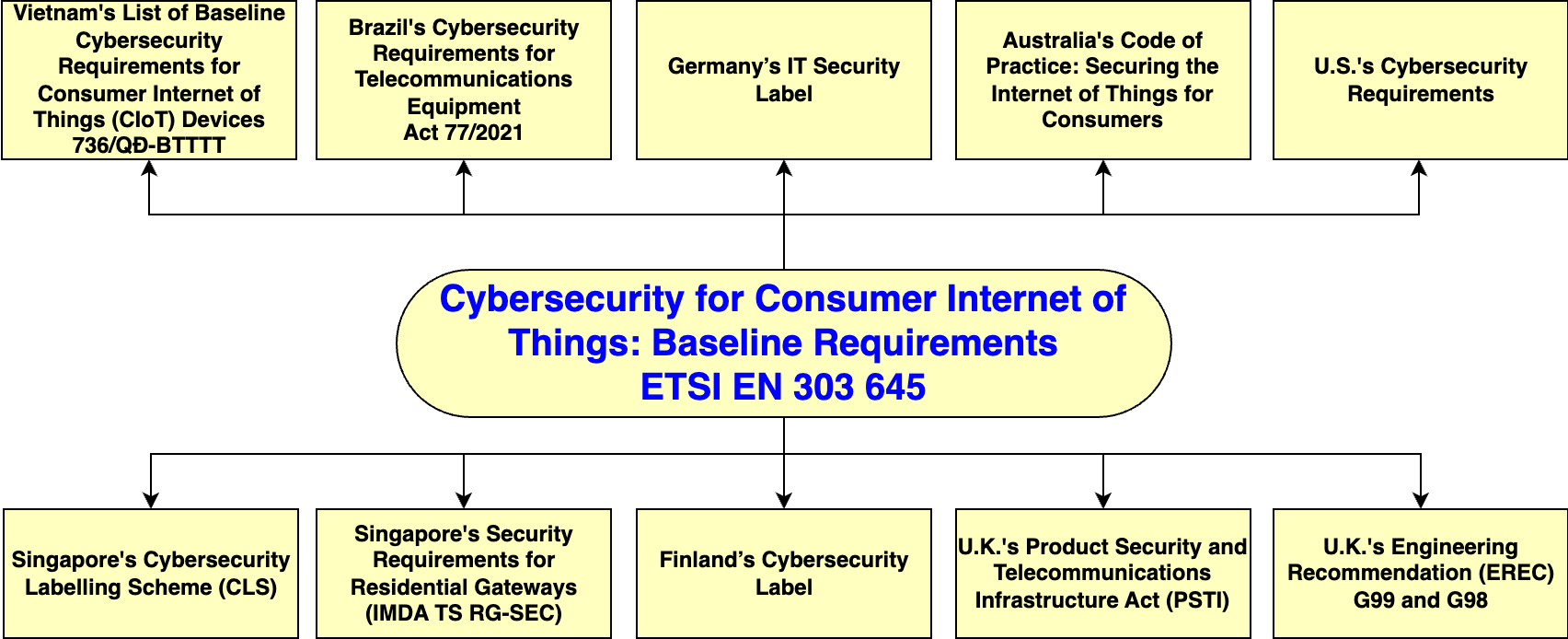
ETSI EN 303 645 has been embraced or cited by many countries, leading to considerable alignment between this standard and the cybersecurity requirements of countries such as Finland, Singapore, Vietnam, Brazil, the United Kingdom, Japan, and more. If your product is already certified under ETSI EN 303 645, you can obtain certification in a specific country or region by meeting distinct requirements that do not overlap.
-
Comparison between ETSI EN 303 645 and Japan’s MIC Article 34-10 Amendment (overlaps marked in green)
-
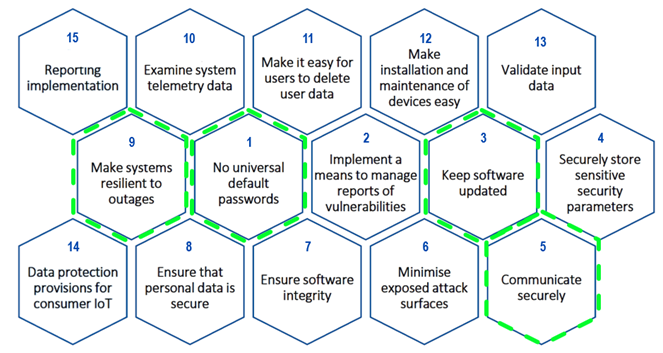
Comparison between ETSI EN 303 645 and Singapore’s IMDA TS RG-SEC (overlaps marked in green)
-
Comparison between ETSI EN 303 645 and Brazil’s Act 77/2021 (overlaps marked in green and specific requirements marked in yellow)
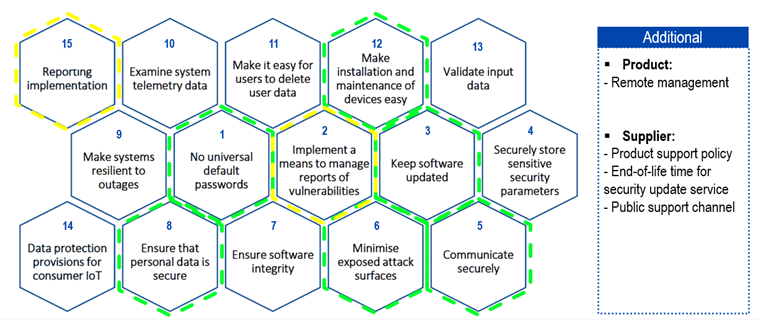
-
Comparison between ETSI EN 303 645 and the U.S.'s NISTIR 8259A (overlaps marked in green)
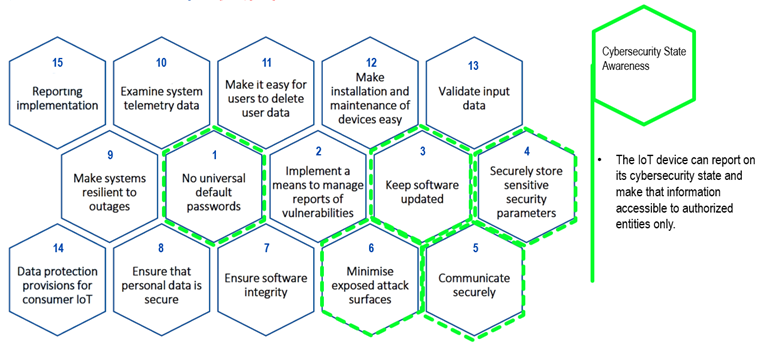
- Singapore’s Cybersecurity Labelling Scheme (CLS) has four levels of rating, corresponding to the provisions specified in ETSI EN 303 645.
- Finland accepts the ETSI EN 303 645 test report as valid for applying for the Finnish Cybersecurity Label.
- There is significant overlap between Brazil’s Minimum Cybersecurity Requirements for Assessing the Conformity of CPE (Customer Premises Equipment) and ETSI EN 303 645.
- U.K.'s PSTI cites the provisions specified in ETSI EN 303 645.
- No universal default passwords (ETSI EN 303 645 Provision 5.1-1 and 5.1-2)
- Implement a means to manage reports of vulnerabilities (ETSI EN 303 645 Provision 5.2-1)
- Keep software updated (ETSI EN 303 645 Provision 5.3-13)
Differences between NISTIR 8425 and NISTIR 8259A
- NISTIR 8259A: IoT Device Cybersecurity Capability Core Baseline
- NISTIR 8425: Profile of the IoT Core Baseline for Consumer IoT Products
Conforming to NISTIR 8259A and NISTIR 8425 allows an IoT product to meet the requirements of federal and state laws in the United States. Additionally, NISTIR 8425 can be used to apply for the U.S. consumer cybersecurity labeling pilots.
NISTIR 8259A device cybersecurity capabilities
Six device cybersecurity capabilities are defined in NISTIR 8259A.
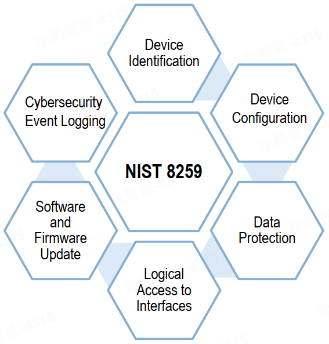
- Device Identification. The ability to uniquely identify devices for management and anti-forgery.
- Device Configuration. The ability for an authorized entity to configure the device security parameters.
- Data Protection. The ability to prevent the user data and security configuration data at rest and in transit from any compromise.
- Logical Access to Interfaces. The ability to restrict access to interfaces to only authorized entities.
- Software and Firmware Update. The ability to employ a secure mechanism for conducting updates to prevent malicious actors from tampering with firmware and software updates, thereby minimizing cybersecurity incidents.
- Cybersecurity Event Logging. The ability to log security events for analysis of cybersecurity incidents or risks and manage vulnerabilities and patches.
NISTIR 8425 product cybersecurity capabilities
Six product cybersecurity capabilities are defined in NISTIR 8425.
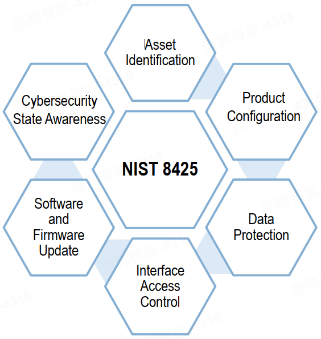
- Asset Identification. The ability to identify IoT products and their components is necessary to support such activities as asset management for updates, data protection, and digital forensics capabilities for incident response.
- Product Configuration. The ability to change the permissions to IoT product configurations can help customers tailor the IoT product’s functionality to their needs and goals. Customers can configure their IoT products to avoid specific threats and risks based on their risk appetite.
- Data Protection. The ability to prevent the user data and security configuration data at rest and in transit from any compromise.
- Interface Access Control. The ability to restrict access to interfaces to only authorized entities.
- Software and Firmware Update. The ability to employ a secure mechanism for conducting updates to prevent malicious actors from tampering with firmware and software updates, thereby minimizing cybersecurity incidents.
- Cybersecurity State Awareness. The IoT product can capture and record information about the state of IoT components that can be used to detect cybersecurity incidents affecting or affected by IoT product components and the data they store and transmit.
The main differences between NISTIR 8259A and NISTIR 8425:
- For NISTIR 8259A, the object under test is the device itself.
- For NISTIR 8425, the objects under test are the device, app, and cloud.
- NISTIR 8259A fully encompasses the security requirements specified in NISTIR 8425, but the testing scope of NISTIR 8425 extends further to include the app and cloud.
Singapore’s mutual recognition with Finland and Germany for cybersecurity labels
A cybersecurity label is designed to help consumers quickly identify the security information of smart products and select smart devices that are less vulnerable to hacking.
Cybersecurity label examples
| Finland | Germany | Singapore | |
|---|---|---|---|
| Cybersecurity label |  |
 |
 |
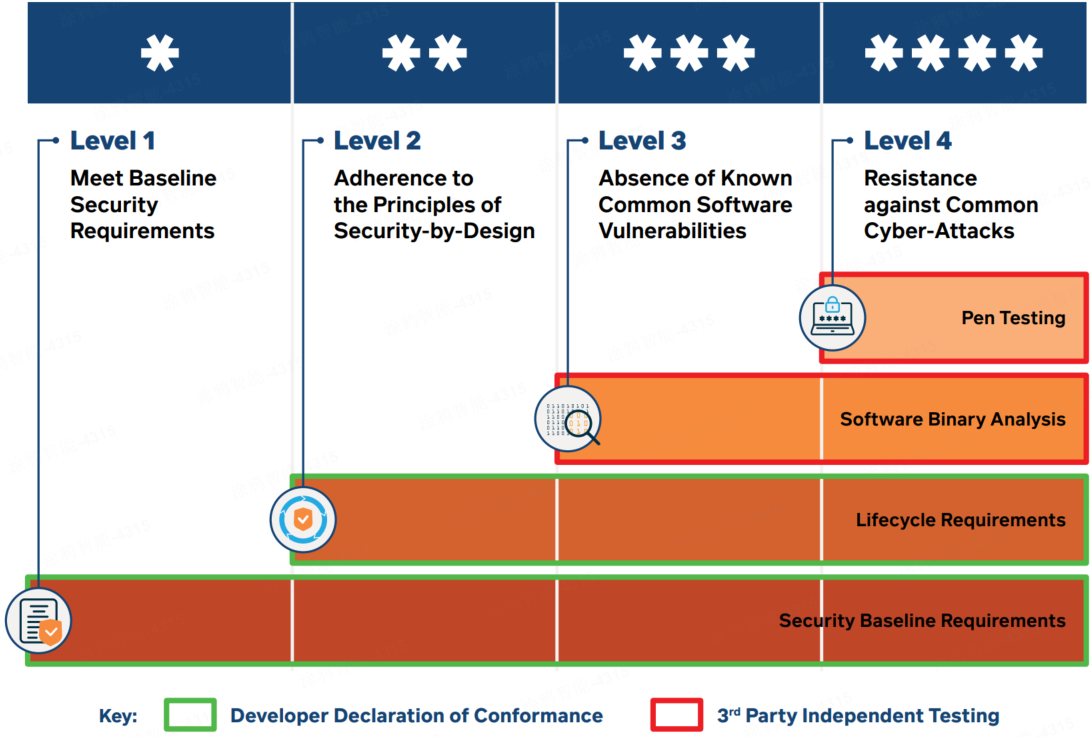
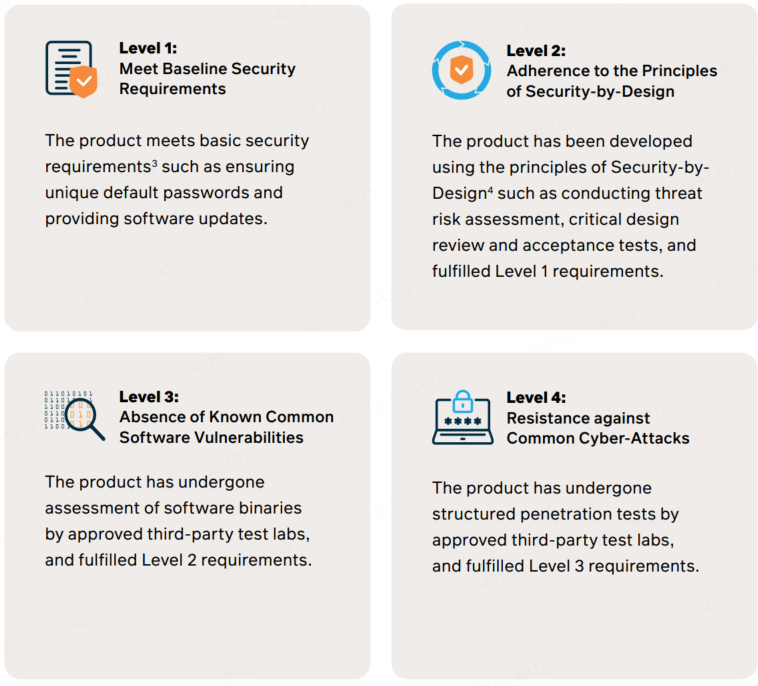
Singapore’s Cybersecurity Labelling Scheme (CLS)
There are four levels of rating under the CLS to indicate the security level of home appliances and smart home devices.
Mutual Recognition: Singapore and Finland
Singapore and Finland have signed a Memorandum of Understanding (MoU) to mutually recognize the Cybersecurity Labels issued by CSA and the Transport and Communications Agency of Finland (Traficom) in 2021. Under the MoU, consumer IoT products that have met the requirements of Finland’s Cybersecurity Label are recognized as having met the requirements of Level 3 of Singapore’s Cybersecurity Labelling Scheme, and products with CLS Level 3 and above are recognized by Finland to have met their requirements.
Level 3 and Level 4 applications for consumer IoT products may be granted both Singapore’s Cybersecurity Labelling Scheme label and the Finnish Cybersecurity Label at once, with a single application process.
Mutual Recognition: Singapore and Germany
Singapore and Germany have signed a Mutual Recognition Arrangement (MRA) to mutually recognize the cybersecurity labels issued by CSA and the Federal Office for Information Security of Germany (BSI) in 2022. Under the MRA, smart consumer products issued with Germany’s IT Security Label will be recognized by CSA to have fulfilled Level 2 of Singapore’s Cybersecurity Labelling Scheme, and products with CLS Level 2 and above are recognized by Germany to have met their requirements.
The mutual recognition of cybersecurity labels will apply to devices intended for use by consumers such as smart cameras, smart TVs, smart speakers, smart toys, smart garden and household robots, gateways and hubs for home automation, health trackers, smart lighting, smart plug (smart power socket), and smart thermostats.
| Country | Level of mutual recognition |
|---|---|
| Finland’s Cybersecurity Label | CLS Level 3 and above |
| Germany’s IT Security Label | CLS Level 2 and above |
Is this page helpful?
YesFeedbackIs this page helpful?
YesFeedback





