Audio and Video Data Security
Last Updated on : 2023-08-09 08:08:56
Audio and video data in transit and data at rest are protected with access control, data encryption, and signature validation.
Concepts
-
Symmetric encryption: Use only one key to encrypt and decrypt data. Be sure to keep the key safe. AES is the dominant algorithm for encrypting data. It comes in various key lengths (such as 128 bits and 256 bits) and modes of operation (such as CBC and ECB).
-
Asymmetric encryption: Use a mathematically related pair of keys, a public key for encryption and a private key for decryption. The private key is used to sign data, and the public key from that pair is used to validate the signature. Be sure to keep the private key safe. Rivest-Shamir-Adleman (RSA) and Elliptic Curve Cryptography (ECC) are the common asymmetric algorithms.
The computational complexity of asymmetric encryption makes it both more secure and generally slower. A hybrid encryption scheme is commonly used, where the symmetric key is encrypted using asymmetric encryption and the data to be transferred is encrypted using symmetric encryption.
-
Hashing algorithm: Use the data cloud to compute a fixed-length hash value from the data segments input. This is a one-way operation, so it is impossible to go backward and find the input given the hash. The hash algorithm is used to generate a digital signature (a.k.a. fingerprint) for data, which prevents tampering with the data while it is in transit or at rest.
-
CA certificate: A server certificate issued by a certificate authority, which the client can use to determine if the cloud service can be trusted to prevent network hijacking.
-
Transport Layer Security (TLS): A cryptographic protocol that protects internet communications. It combines symmetric encryption, asymmetric encryption, authentication, digital signatures, and certificate validation. TLS is a protocol that sits between the TCP/UDP layer and the application layer, such as HTTP over TLS (HTTPS) or a secure channel.
Security of streaming data transmission
Tuya’s proprietary P2P technology is used for audio and video preview, as well as two-way talk. The following diagram shows a simplified P2P session process:
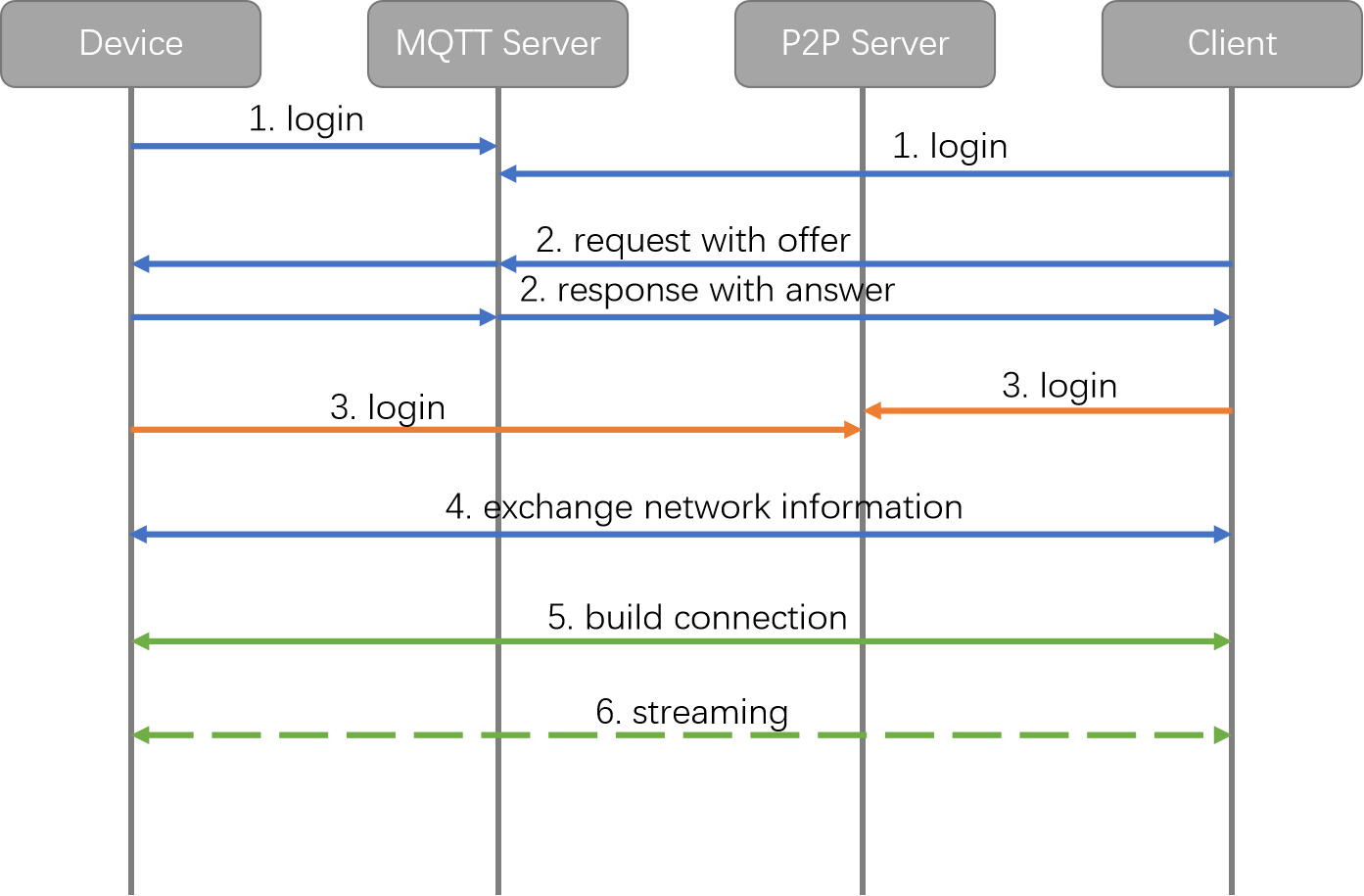
It includes the following security mechanisms:
- Both the camera and the mobile app (client) must be authenticated before logging in to Tuya’s MQTT cloud service.
- The camera and client exchange P2P messages (offer and answer) through an encrypted MQTT over TLS channel, using the ECC algorithm for TLS encryption.
- Before a connection attempt, determine if both the camera and client have the necessary permissions to access the P2P server, including STUN and TURN services.
- When the camera and client exchange network information to create a P2P session, their identities are verified again to prevent attacks.
- During streaming, each data packet is encrypted with AES and signed with HMAC.
Security of audio and video data storage
After the user enables services such as human and pet detection alerts and cloud storage, the camera will upload videos, images, and other files to the cloud object storage server. The following diagram shows a simplified process (excluding the process of subscribing to a service on the client):
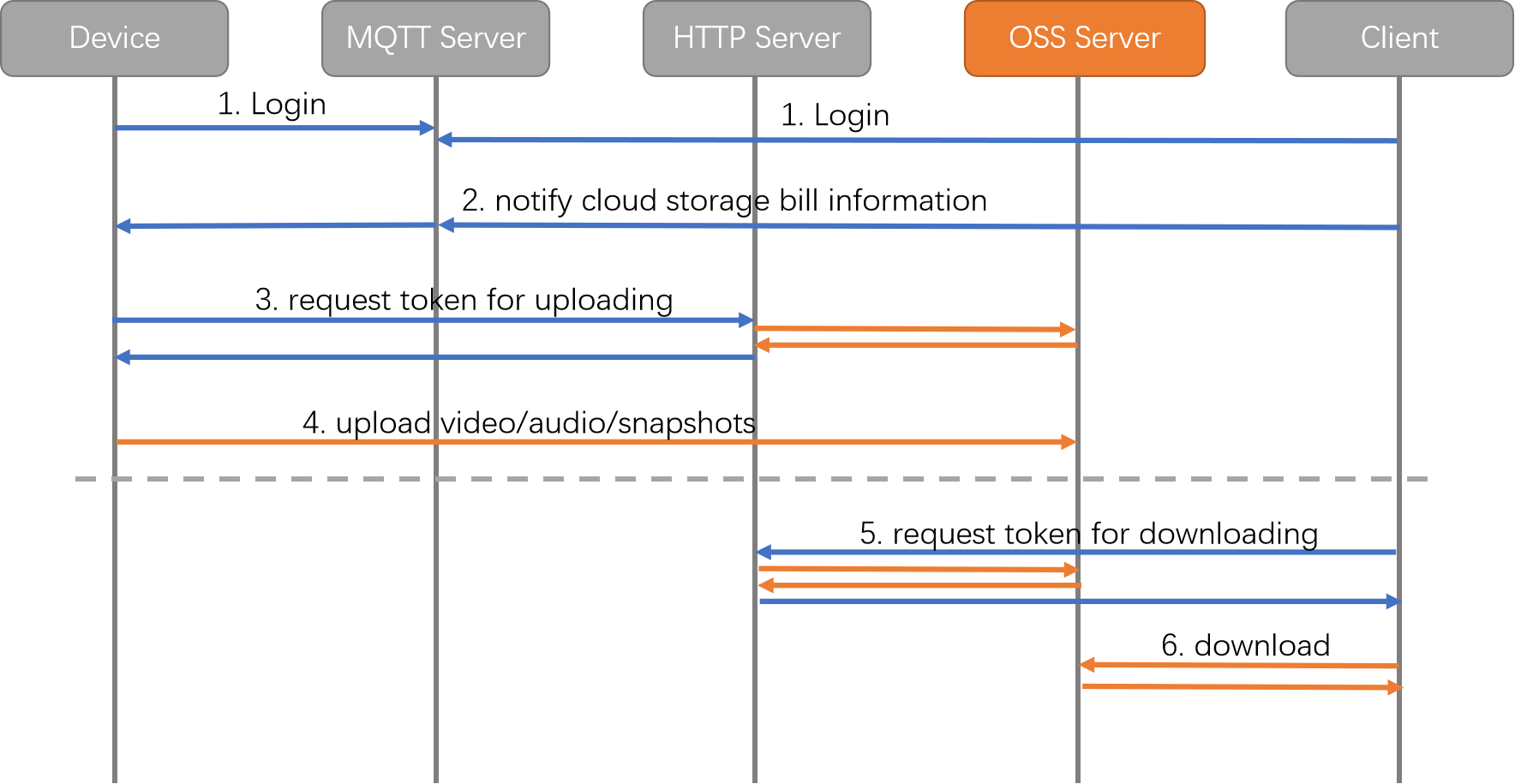
It includes the following security mechanisms:
- Both the camera and the mobile app (client) must be authenticated before logging in to Tuya’s MQTT cloud service.
- The camera requests and updates the status of the cloud storage order from the server through HTTPS, using the ECC algorithm for TLS encryption.
- The permissions to add, delete, and modify files in the object storage service (OSS) are managed in the cloud. The camera and client get temporary tokens through HTTPS when uploading or downloading files.
- The camera uploads audio and video data to the OSS server through HTTPS.
- Audio and video data is encrypted using AES encryption.
- A unique key is generated in the cloud for each device. This key is then sent to the device and client using HTTPS, with double encryption and an MD5 integrity check.
Is this page helpful?
YesFeedbackIs this page helpful?
YesFeedback





